CVEFeed Newsroom – Latest Cybersecurity Updates
The "Cyber Newsroom Feed" module is a live feed of the latest cyber news enriched with CVE and vulnerability data. The feed is updated every 5 minutes and includes the latest news from the cyber security industry. The feed is designed to provide users with a comprehensive overview of the latest cyber security news and trends.

-
Hot for Security
French submarine secrets surface after cyber attack
European defence giant Naval Group has confirmed that it is investigating an alleged cyber attack which has seen what purports to be sensitive internal data published on the internet by hackers.Naval ...
-
BleepingComputer
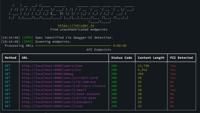
Free Tool Autoswagger Finds The API Flaws Attackers Hope You Miss
APIs: Still Easy Targets in 2025 APIs are the backbone of modern applications - and one of the most exposed parts of an organization’s infrastructure. This makes them a prime target for attackers. One ...
-
Schneier on Security
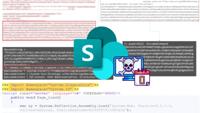
Microsoft SharePoint Zero-Day
Chinese hackers are exploiting a high-severity vulnerability in Microsoft SharePoint to steal data worldwide: The vulnerability, tracked as CVE-2025-53770, carries a severity rating of 9.8 out of a po ...
-
CybersecurityNews
New “ToolShell” Exploit Chain Attacking SharePoint Servers to Gain Complete Control
A critical new threat targeting Microsoft SharePoint servers through a sophisticated exploit chain dubbed “ToolShell.” This multi-stage attack combines previously patched vulnerabilities with fresh ze ...

-
CybersecurityNews
LG Innotek Camera Vulnerabilities Let Attackers Gain Administrative Access
A serious security vulnerability has been discovered in LG Innotek’s LNV5110R camera model that could allow cybercriminals to gain complete administrative control over affected devices. The U.S. Cyber ...

-
CybersecurityNews
Critical Salesforce Tableau Vulnerabilities Let Attackers Execute Code Remotely
Multiple critical security vulnerabilities affecting Salesforce’s Tableau Server that could allow attackers to execute remote code, bypass authorization controls, and access sensitive production datab ...
-
The Hacker News
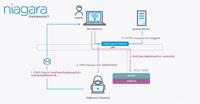
Critical Flaws in Niagara Framework Threaten Smart Buildings and Industrial Systems Worldwide
Cybersecurity researchers have discovered over a dozen security vulnerabilities impacting Tridium's Niagara Framework that could allow an attacker on the same network to compromise the system under ce ...

-
TheCyberThrone
VMware Tools VGAuth Vulnerabilities
Skip to content July 28, 2025Overview:Two critical local privilege escalation vulnerabilities were recently discovered in the VGAuth service component of VMware Tools for Windows virtual machines (VMs ...

-
Daily CyberSecurity
Critical Command Injection (CVE-2025-54416) in tj-actions/branch-names GitHub Action Exposes 5,000+ Repos
A critical command injection vulnerability has been disclosed in the widely used GitHub Action tj-actions/branch-names, affecting over 5,000 public repositories. Assigned CVE-2025-54416 with a CVSS sc ...
-
Daily CyberSecurity
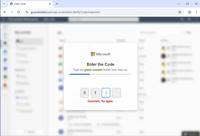
The Homograph Illusion: Phishing Attacks Exploit Lookalike Characters to Bypass Defenses – AI Amplifies the Threat
The OTP code is dynamic and changes on each keypress to filter out bots and crawlers | Image: Unit 42 In a new report, Palo Alto Networks’ Unit 42 has unveiled an insidious phishing technique that con ...


