CVE-2025-8088
RARLAB WinRAR Path Traversal Vulnerability - [Actively Exploited]
Description
A path traversal vulnerability affecting the Windows version of WinRAR allows the attackers to execute arbitrary code by crafting malicious archive files. This vulnerability was exploited in the wild and was discovered by Anton Cherepanov, Peter Košinár, and Peter Strýček from ESET.
INFO
Published Date :
Aug. 8, 2025, 12:15 p.m.
Last Modified :
Oct. 30, 2025, 3:50 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
RARLAB WinRAR contains a path traversal vulnerability affecting the Windows version of WinRAR. This vulnerability could allow an attacker to execute arbitrary code by crafting malicious archive files.
Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable.
https://www.win-rar.com/singlenewsview.html?&L=0&tx_ttnews%5Btt_news%5D=283&cHash=a64b4a8f662d3639dec8d65f47bc93c5 ; https://nvd.nist.gov/vuln/detail/CVE-2025-8088
Affected Products
The following products are affected by CVE-2025-8088
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | HIGH | [email protected] | ||||
| CVSS 4.0 | HIGH | [email protected] |
Solution
- Update WinRAR to the latest version available.
- Avoid opening archives from untrusted sources.
Public PoC/Exploit Available at Github
CVE-2025-8088 has a 70 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2025-8088.
| URL | Resource |
|---|---|
| https://www.win-rar.com/singlenewsview.html?&L=0&tx_ttnews%5Btt_news%5D=283&cHash=a64b4a8f662d3639dec8d65f47bc93c5 | Release Notes |
| https://arstechnica.com/security/2025/08/high-severity-winrar-0-day-exploited-for-weeks-by-2-groups/ | Press/Media Coverage |
| https://support.dtsearch.com/faq/dts0245.htm | Third Party Advisory |
| https://www.vicarius.io/vsociety/posts/cve-2025-8088-detect-winrar-zero-day | Third Party Advisory |
| https://www.vicarius.io/vsociety/posts/cve-2025-8088-mitigate-winrar-zero-day-using-srp-and-ifeo | Mitigation Third Party Advisory |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-8088 | US Government Resource |
| https://www.welivesecurity.com/en/eset-research/update-winrar-tools-now-romcom-and-others-exploiting-zero-day-vulnerability/#the-discovery-of-cve-2025-8088 | Press/Media Coverage |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2025-8088 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2025-8088
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
Laboratorio PoC Exploit RAR (Path Traversal / Injection ) - CVE2025-8088 / 2025-6218
Python
Rust library that detects files which look normal but have been crafted to exploit parsing vulnerabilities
exploit mobile
Rust
Defensive PowerShell tool for static inspection of RAR archives and detection of CVE-2025-8088 path traversal anomalies.
PowerShell
CVE 2025 8088
cve-2025-8088 font hacking
Python
None
🛠 Exploit CVE-2025-8088 with this Python tool to generate malicious WinRAR archives that ensure payload persistence in Windows startup folders.
cve cve-2025-8088 cybersecurity exploit poc redteam security-research vulnerability vunerability winrar zero-day zeroday
Python
Лабораторная работа №2 Разбор методик эксплуатации уязвимостей
Comprehensive analysis and proof-of-concept for CVE-2025-6218 - WinRAR path traversal RCE vulnerability affecting versions 7.11 and earlier
Python PowerShell
None
Python
Path traversal tool based on cve-2025-8088
cve-2025-8088
Python
Path traversal tool based on cve 2025 8088
cve-2025-8088
Python
path traversal tool based on cve-2025-8088
cve-2025-8088
Python
Path traversal tool based on CVE-2025-8088
cve-2025-8088
Python
path traversal tool based on cve-2025-8088 vulnerability
cve-2025-8088
Python
Path traversal tool based on CVE-2025-8088 vulnerability
cve cve-2025-8088
Python
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2025-8088 vulnerability anywhere in the article.
-
The Hacker News
Critical n8n Flaw CVE-2026-25049 Enables System Command Execution via Malicious Workflows
A new, critical security vulnerability has been disclosed in the n8n workflow automation platform that, if successfully exploited, could result in the execution of arbitrary system commands. The flaw, ... Read more

-
The Hacker News
Hackers Exploit React2Shell to Hijack Web Traffic via Compromised NGINX Servers
Cybersecurity researchers have disclosed details of an active web traffic hijacking campaign that has targeted NGINX installations and management panels like Baota (BT) in an attempt to route it throu ... Read more

-
CybersecurityNews
Amaranth-Dragon Exploiting WinRAR Vulnerability to Gain Persistent to Victim Systems
A sophisticated cyber-espionage group known as Amaranth-Dragon has launched a series of highly targeted attacks against government and law enforcement agencies across Southeast Asia. Active throughout ... Read more

-
Daily CyberSecurity
10 Days to Exploit: Amaranth-Dragon Weaponizes WinRAR Flaw to Spy on SE Asia
A new and relentless cyber-espionage campaign is sweeping across government and law enforcement agencies in Southeast Asia, driven by a threat group that wastes no time in weaponizing freshly disclose ... Read more

-
The Hacker News
China-Linked Amaranth-Dragon Exploits WinRAR Flaw in Espionage Campaigns
Threat actors affiliated with China have been attributed to a fresh set of cyber espionage campaigns targeting government and law enforcement agencies across Southeast Asia throughout 2025. Check Poin ... Read more

-
The Hacker News
CISA Adds Actively Exploited SolarWinds Web Help Desk RCE to KEV Catalog
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a critical security flaw impacting SolarWinds Web Help Desk (WHD) to its Known Exploited Vulnerabilities (KEV) catalog ... Read more

-
The Hacker News
Hackers Exploit Metro4Shell RCE Flaw in React Native CLI npm Package
Threat actors have been observed exploiting a critical security flaw impacting the Metro Development Server in the popular "@react-native-community/cli" npm package. Cybersecurity company VulnCheck sa ... Read more

-
The Hacker News
APT28 Uses Microsoft Office CVE-2026-21509 in Espionage-Focused Malware Attacks
The Russia-linked state-sponsored threat actor known as APT28 (aka UAC-0001) has been attributed to attacks exploiting a newly disclosed security flaw in Microsoft Office as part of a campaign codenam ... Read more

-
europa.eu
Cyber Brief 26-02 - January 2026
Cyber Brief (January 2026)February 2, 2026 – Version: 1TLP:CLEARExecutive summaryWe analysed 268 open source reports for this Cyber Security Brief.1Relating to cyber policy, The European Commission pr ... Read more

-
The Hacker News
OpenClaw Bug Enables One-Click Remote Code Execution via Malicious Link
A high-severity security flaw has been disclosed in OpenClaw (formerly referred to as Clawdbot and Moltbot) that could allow remote code execution (RCE) through a crafted malicious link. The issue, wh ... Read more

-
Help Net Security
Week in review: Microsoft fixes exploited Office zero-day, Fortinet patches FortiCloud SSO flaw
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: When open science meets real-world cybersecurity In this Help Net Security interview, Matthew Kwiatkow ... Read more

-
The Cyber Express
The Cyber Express Weekly Roundup: Threats, Regulations, and Digital Security Trends
As January 2026 comes to a close, The Cyber Express takes a comprehensive look at the events defining the global cybersecurity landscape. Over the past week, organizations worldwide faced high-profile ... Read more

-
The Cyber Express
Ivanti Patches Two Zero-Days in Mobile Manager After Attackers Exploit Vulnerable Systems
Two code injection vulnerabilities allowed unauthenticated attackers to execute arbitrary code and access sensitive device information across compromised networks. Ivanti released emergency patches fo ... Read more

-
The Cyber Express
Cyble Research Discovers ShadowHS, an In-Memory Linux Framework for Long-Term Access
Cyble Research & Intelligence Labs (CRIL) has uncovered a post-exploitation Linux framework called ShadowHS, designed for stealthy, in-memory operations. Unlike traditional malware, ShadowHS leverages ... Read more

-
The Cyber Express
Nation-State Hackers, Cybercriminals Weaponize Patched WinRAR Flaw Despite Six-Month-Old Fix
Russian and Chinese espionage groups continue to exploit an N-day vulnerability (CVE-2025-8088) in WinRAR alongside financially motivated actors, all leveraging a path traversal vulnerability that dro ... Read more
-
Help Net Security
SolarWinds fixes critical Web Help Desk RCE vulnerabilities, upgrade ASAP!
SolarWinds has fixed six critical and high-severity vulnerabilities in its popular Web Help Desk (WHD) support ticketing and asset management solution, and is urging customers to upgrade to v2026.1 as ... Read more

-
Daily CyberSecurity
CVE-2026-24002: Critical Sandbox Escape Turns Grist Spreadsheets into RCE Weapons
A seemingly innocent spreadsheet formula could be the key to compromising entire organizations, thanks to a critical vulnerability uncovered by Cyera Research Labs in Grist-Core. The flaw, tracked as ... Read more
-
Daily CyberSecurity
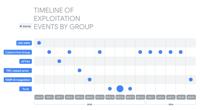
The “Zeroplayer” Arsenal: WinRAR Flaw CVE-2025-8088 Weaponized by Spies
Timeline of notable observed exploitation | Image: GTIG A critical vulnerability in one of the world’s most popular file archivers has become a favorite weapon for government spies and cybercriminals ... Read more

-
The Register
Everybody is WinRAR phishing, dropping RATs as fast as lightning
Come one, come all. Everyone from Russian and Chinese government goons to financially motivated miscreants is exploiting a long-since-patched WinRAR vuln to bring you infostealers and Remote Access Tr ... Read more

-
hackread.com
Hackers Still Using Patched WinRAR Flaw for Malware Drops, Warns Google
The Google Threat Intelligence Group (GTIG) warns that nation-state actors and financially motivated threat actors are exploiting a flaw in WinRAR. Known as CVE-2025-8088, this vulnerability allows ha ... Read more
The following table lists the changes that have been made to the
CVE-2025-8088 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 30, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-8088 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-8088 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-8088 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-8088 -
Modified Analysis by [email protected]
Sep. 16, 2025
Action Type Old Value New Value Added Reference Type CVE: https://arstechnica.com/security/2025/08/high-severity-winrar-0-day-exploited-for-weeks-by-2-groups/ Types: Press/Media Coverage -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Sep. 15, 2025
Action Type Old Value New Value Added Reference https://arstechnica.com/security/2025/08/high-severity-winrar-0-day-exploited-for-weeks-by-2-groups/ -
Modified Analysis by [email protected]
Aug. 21, 2025
Action Type Old Value New Value Added CPE Configuration AND OR *cpe:2.3:a:dtsearch:dtsearch:*:*:*:*:*:*:*:* versions up to (excluding) 2023.01 OR cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:* Added Reference Type CVE: https://support.dtsearch.com/faq/dts0245.htm Types: Third Party Advisory -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Aug. 21, 2025
Action Type Old Value New Value Added Reference https://support.dtsearch.com/faq/dts0245.htm -
Modified Analysis by [email protected]
Aug. 18, 2025
Action Type Old Value New Value Added Reference Type CVE: https://www.vicarius.io/vsociety/posts/cve-2025-8088-detect-winrar-zero-day Types: Third Party Advisory Added Reference Type CVE: https://www.vicarius.io/vsociety/posts/cve-2025-8088-mitigate-winrar-zero-day-using-srp-and-ifeo Types: Mitigation, Third Party Advisory -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Aug. 15, 2025
Action Type Old Value New Value Added Reference https://www.vicarius.io/vsociety/posts/cve-2025-8088-detect-winrar-zero-day Added Reference https://www.vicarius.io/vsociety/posts/cve-2025-8088-mitigate-winrar-zero-day-using-srp-and-ifeo -
CVE Modified by [email protected]
Aug. 15, 2025
Action Type Old Value New Value Changed Description A path traversal vulnerability affecting the Windows version of WinRAR allows the attackers to execute arbitrary code by crafting malicious archive files. This vulnerability was exploited in the wild and was discovered by Anton Cherepanov, Peter Košinár, and Peter Strý?ek from ESET. A path traversal vulnerability affecting the Windows version of WinRAR allows the attackers to execute arbitrary code by crafting malicious archive files. This vulnerability was exploited in the wild and was discovered by Anton Cherepanov, Peter Košinár, and Peter Strýček from ESET. -
Initial Analysis by [email protected]
Aug. 13, 2025
Action Type Old Value New Value Added CVSS V3.1 AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H Added CPE Configuration AND OR *cpe:2.3:a:rarlab:winrar:*:*:*:*:*:*:*:* versions up to (excluding) 7.13 OR cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:* Added Reference Type ESET: https://www.win-rar.com/singlenewsview.html?&L=0&tx_ttnews%5Btt_news%5D=283&cHash=a64b4a8f662d3639dec8d65f47bc93c5 Types: Release Notes Added Reference Type CISA-ADP: https://www.welivesecurity.com/en/eset-research/update-winrar-tools-now-romcom-and-others-exploiting-zero-day-vulnerability/#the-discovery-of-cve-2025-8088 Types: Press/Media Coverage -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Aug. 13, 2025
Action Type Old Value New Value Added Date Added 2025-08-12 Added Due Date 2025-09-02 Added Required Action Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable. Added Vulnerability Name RARLAB WinRAR Path Traversal Vulnerability -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Aug. 12, 2025
Action Type Old Value New Value Added Reference https://www.welivesecurity.com/en/eset-research/update-winrar-tools-now-romcom-and-others-exploiting-zero-day-vulnerability/#the-discovery-of-cve-2025-8088 -
New CVE Received by [email protected]
Aug. 08, 2025
Action Type Old Value New Value Added Description A path traversal vulnerability affecting the Windows version of WinRAR allows the attackers to execute arbitrary code by crafting malicious archive files. This vulnerability was exploited in the wild and was discovered by Anton Cherepanov, Peter Košinár, and Peter Strýček from ESET. Added CVSS V4.0 AV:L/AC:L/AT:N/PR:N/UI:A/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N/E:X/CR:X/IR:X/AR:X/MAV:X/MAC:X/MAT:X/MPR:X/MUI:X/MVC:X/MVI:X/MVA:X/MSC:X/MSI:X/MSA:X/S:X/AU:X/R:X/V:X/RE:X/U:X Added CWE CWE-35 Added Reference https://www.win-rar.com/singlenewsview.html?&L=0&tx_ttnews%5Btt_news%5D=283&cHash=a64b4a8f662d3639dec8d65f47bc93c5


